NIS2 Compliance Dashboard
Real-time monitoring of your NTFS security compliance status
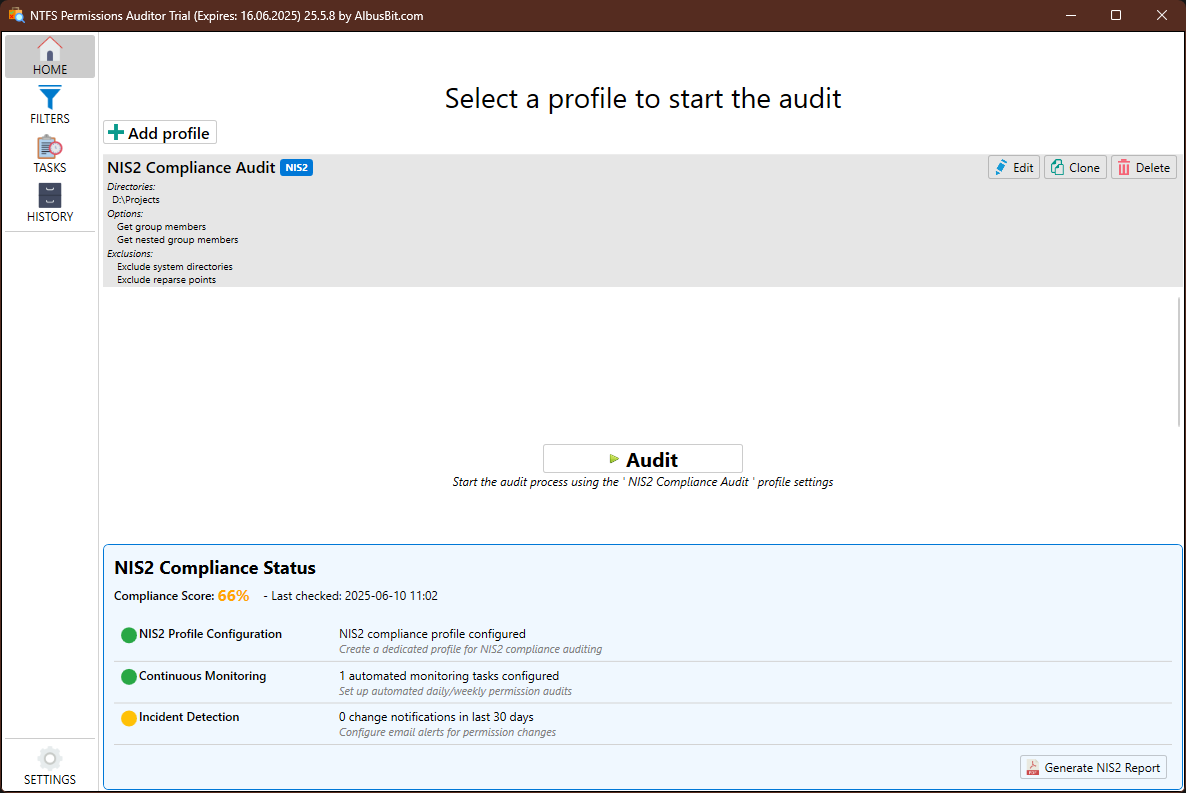
Compliance Score
Overall compliance percentage based on NIS2 requirements for file system security
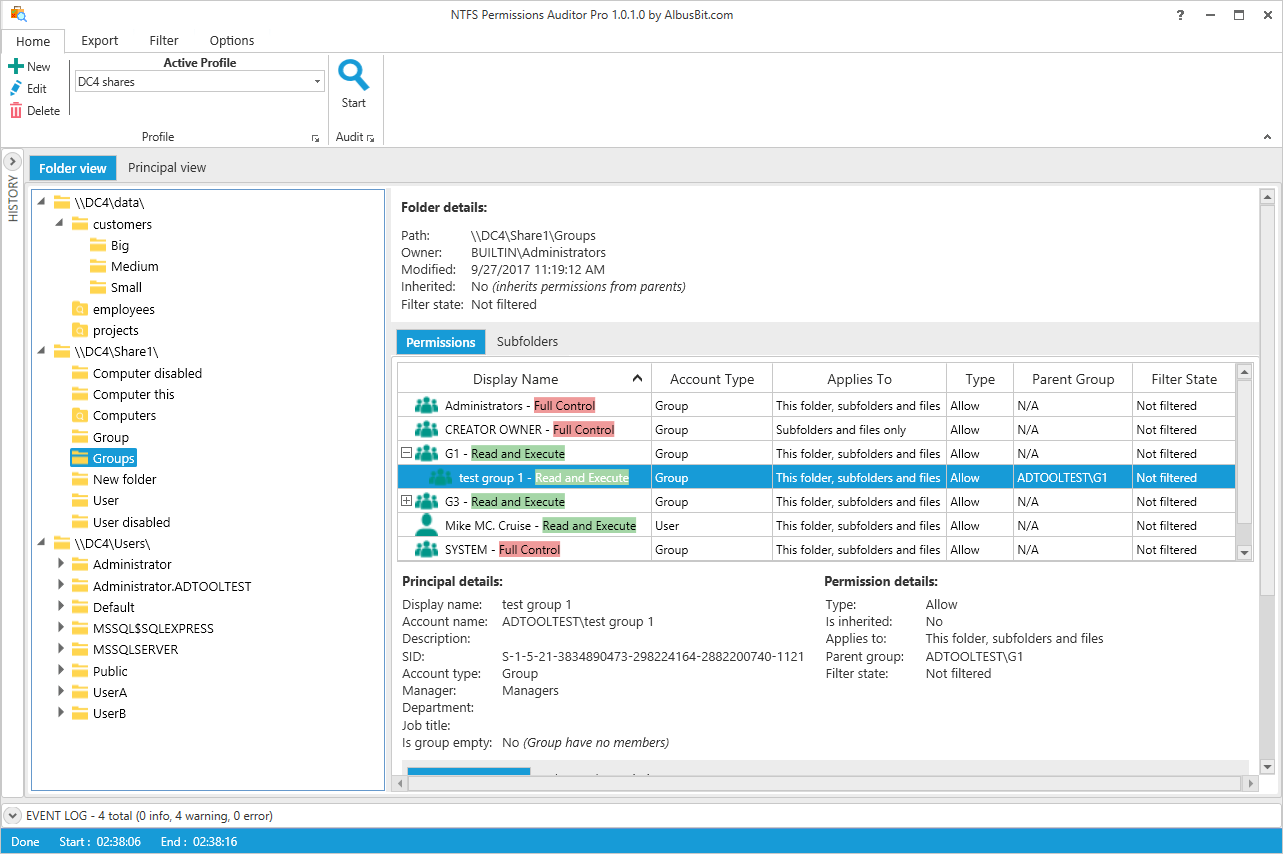
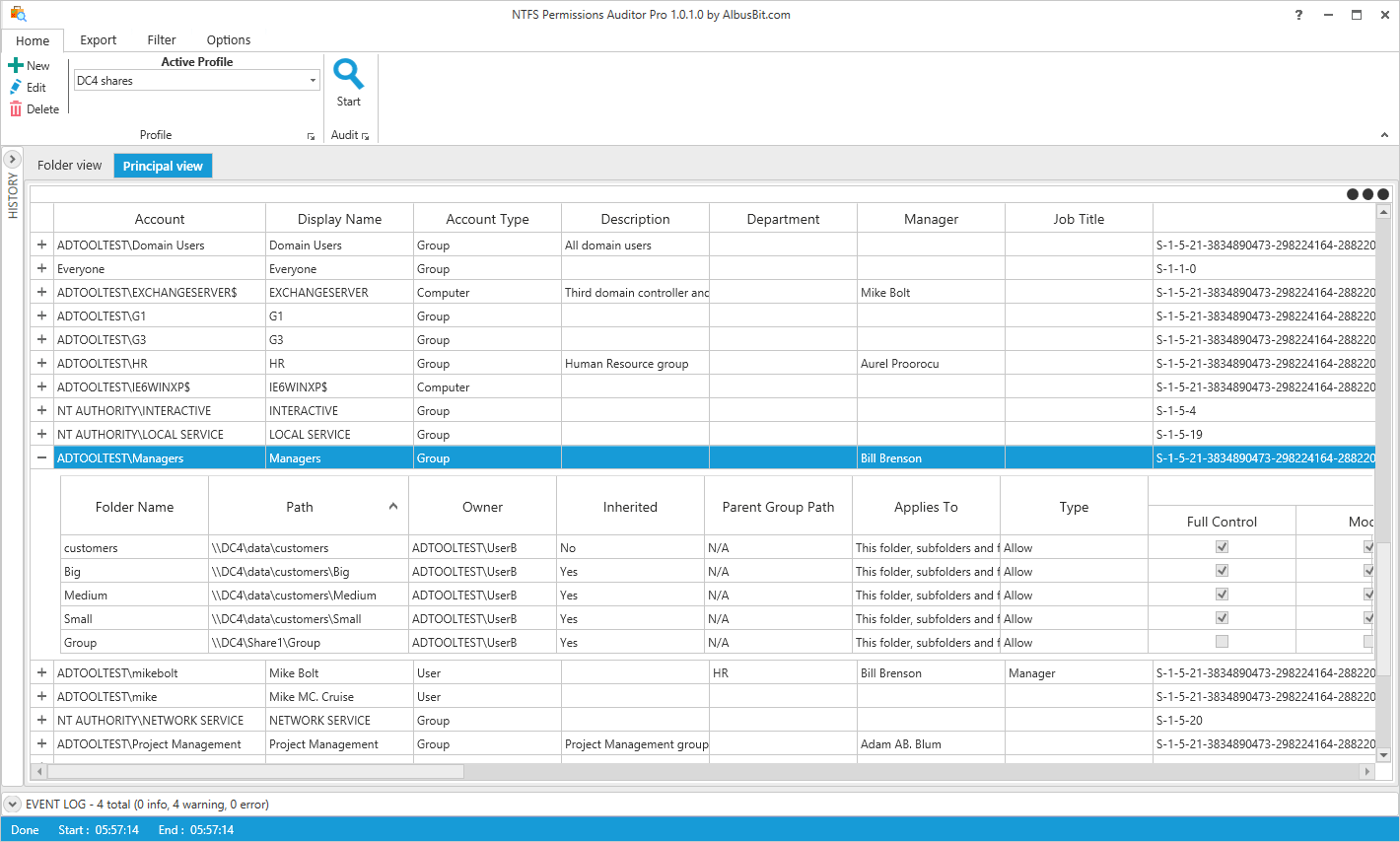
Profile Configuration
Track NIS2-specific audit profiles covering critical infrastructure folders
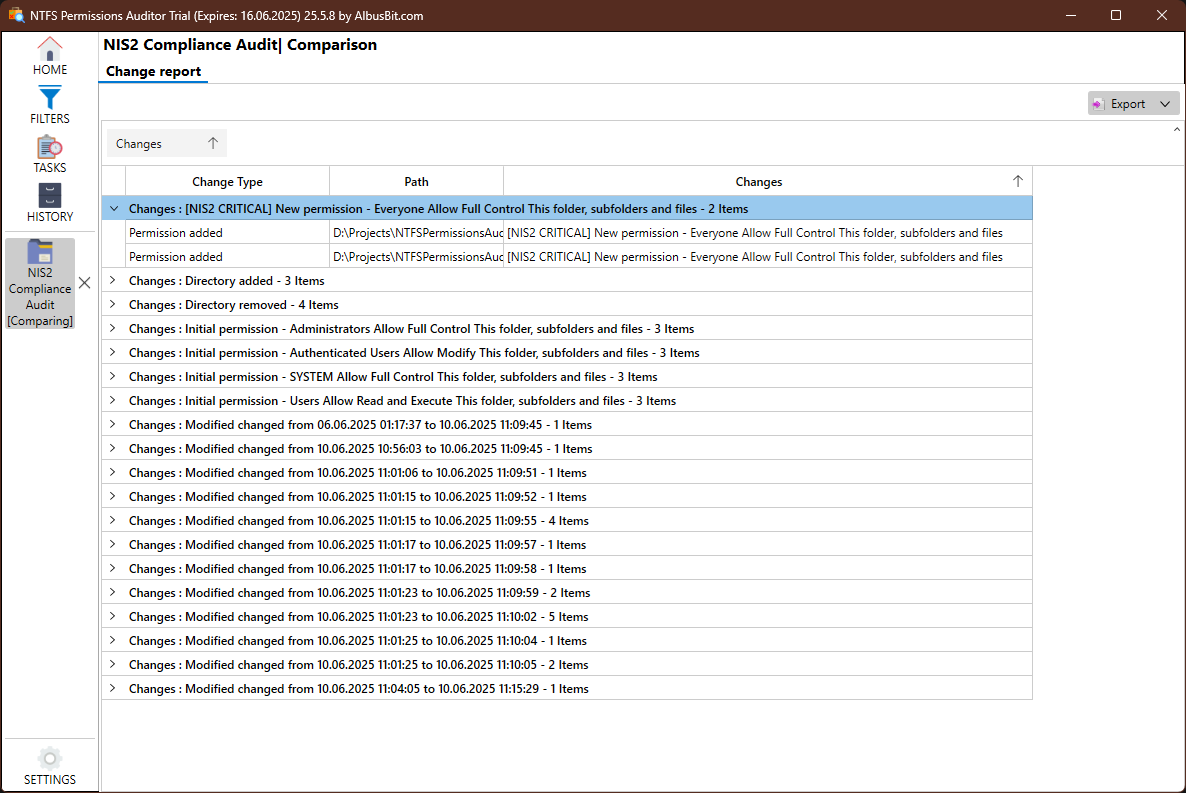
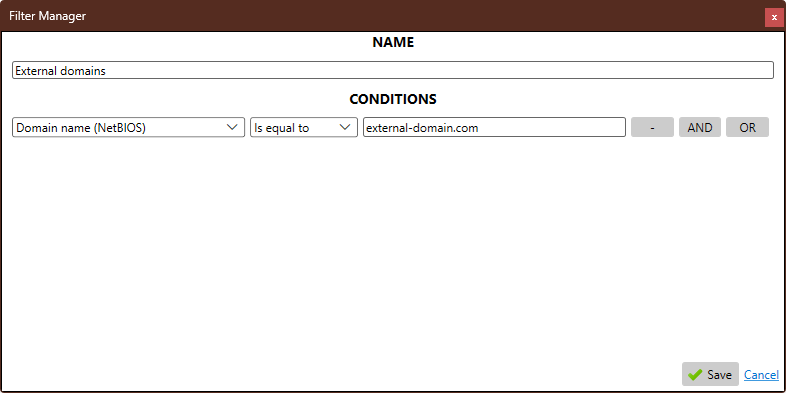
Continuous Monitoring
Automated task scheduling ensures regular compliance checks
Incident Detection
Email alerts for critical permission changes requiring investigation