Correctly setting up file access permissions is a crucial step in securing a Windows system. It ensures that the right people have to access the files and information they need, reducing the likelihood of accidental deletions or data leaks.
If you’re a Windows user, you’ve probably heard of NTFS permissions. But, what are they? How do they work? How can you set up NTFS permissions correctly?
In this blog post, we’ll answer all of your questions about NTFS permissions and discuss some best practices for getting Windows permissions right.
Quick Solution: Need to quickly understand who has access to what files? Download our free NTFS Permissions Auditor and get a complete permissions map in just 5 minutes.
Table of Contents
- What are NTFS permissions?
- NTFS vs. Share Permissions: What's the Difference?
- How do NTFS permissions work?
- Inheritance vs. Explicit Permissions
- What are the different types of NTFS permissions?
- How NTFS Permissions Are Evaluated?
- How can I set up NTFS permissions?
- How to Fix Common NTFS Permission Problems?
- What are some best practices for using NTFS permissions?
- NTFS Permission Best Practices for Businesses
- How to audit and understand the current situation with NTFS permissions?
- Frequently Asked Questions About NTFS Permissions
- Final Thoughts
What are NTFS permissions?
NTFS permissions are a type of access control that can be used to restrict who can access files and folders on a computer or network. NTFS permissions can be applied to both local and network resources.
These permissions are available to any drive formatted with NTFS (New Technology File System) - the default file system for Windows. For instance, if a drive is formatted with the FAT32 file system, NTFS permissions will not be available.
They’re particularly useful as these permissions can be granted to both individual users and groups - for both local users and network users.
NTFS vs. Share Permissions: What's the Difference?
Many IT professionals confuse NTFS and share permissions or don't understand how they work together. Here's a quick comparison:
| Feature | NTFS Permissions | Share Permissions |
|---|---|---|
| Applied to | Local files and folders | Network shares only |
| Available permissions | Full Control, Modify, Read & Execute, Read, Write, Special Permissions | Full Control, Change, Read |
| Granularity | Highly granular with special permissions | Limited to three basic permissions |
| Used when accessing via | Both local access and network | Network access only |
| When both exist | Most restrictive permission applies | |
When a user accesses a file through a network share, both share permissions and NTFS permissions are evaluated. The most restrictive permission is applied, which is why understanding both systems is crucial for effective security management.
How do NTFS permissions work?
NTFS permissions work by assigning permissions to users and groups. When a user tries to access a resource, the system checks to see if that user has the required permissions. If this isn't the case, they'll be denied access.
This allows the file system to exert control over which users can perform operations on specific drives or within directories.
Many people confuse NTFS permissions with share permissions. In actuality, NTFS permissions offer much better granular control over giving directory access to users and groups - whereas share permissions are limited to Read, Change or Full Control.
The plethora of permission types gives system administrators the ability to control exactly what certain users can do - allowing them very specific access without comprising the file security of the directory referenced.
Inheritance vs. Explicit Permissions
Understanding inheritance is key to mastering NTFS permissions. By default, permissions are inherited from parent folders to subfolders and files. This creates a hierarchical permission structure that simplifies administration.
- Automatically flow from parent to child objects
- Appear dimmed in the permissions interface
- Cannot be modified directly at the child level
- Simplify permissions management
- Changes at parent level affect all children
- Directly applied to a specific file or folder
- Appear in normal text in the permissions interface
- Can be different from parent permissions
- Override inherited permissions
- Remain even if parent permissions change
To break inheritance, open the Advanced Security Settings, click "Disable inheritance," and choose to either convert inherited permissions to explicit permissions or remove them completely.
What are the different types of NTFS permissions?
There are two categories of NTFS permissions - basic and advanced. Most users will be able to effectively control file security using these few basic permission types, but network administrators looking for even more control should consider a few of the advanced parameters.
The basic permissions include:
- Full control: Users can read, write, execute and delete these files and folders. As the name suggests, this gives the user full control over that specific directory or drive - including changing permissions for subdirectories and files within that drive or area.
- Modify: Users can modify and delete files, file properties and folders within the directory.
- Read and execute: Users can read files and run executables and scripts.
- Read: Users can view files within the directory. They cannot modify or delete these files or their properties.
- Write: Users can add new files and folders to the directory and write to existing files.
Most system administrators stick to these basic permissions, but specific workflows may require more granular control.
Special permissions are accessed through the Advanced Security Settings in Windows Explorer. They include:
- List Folder/Read Data: Users can view file and subfolder names and data in files.
- Read Attributes: Users can view the attributes of a file or folder.
- Create Files: Users can create files in the directory, without granting permission to modify existing files.
- Write Attributes: Users can make changes to the attributes of an existing file or folder.
- Read/Change Permissions: Users can view, or change the NTFS permissions granted to a directory or file.
This isn’t an exhaustive list. You can view the full range of special permissions in the Advanced Security Settings tab. We’ll walk you through that process below.
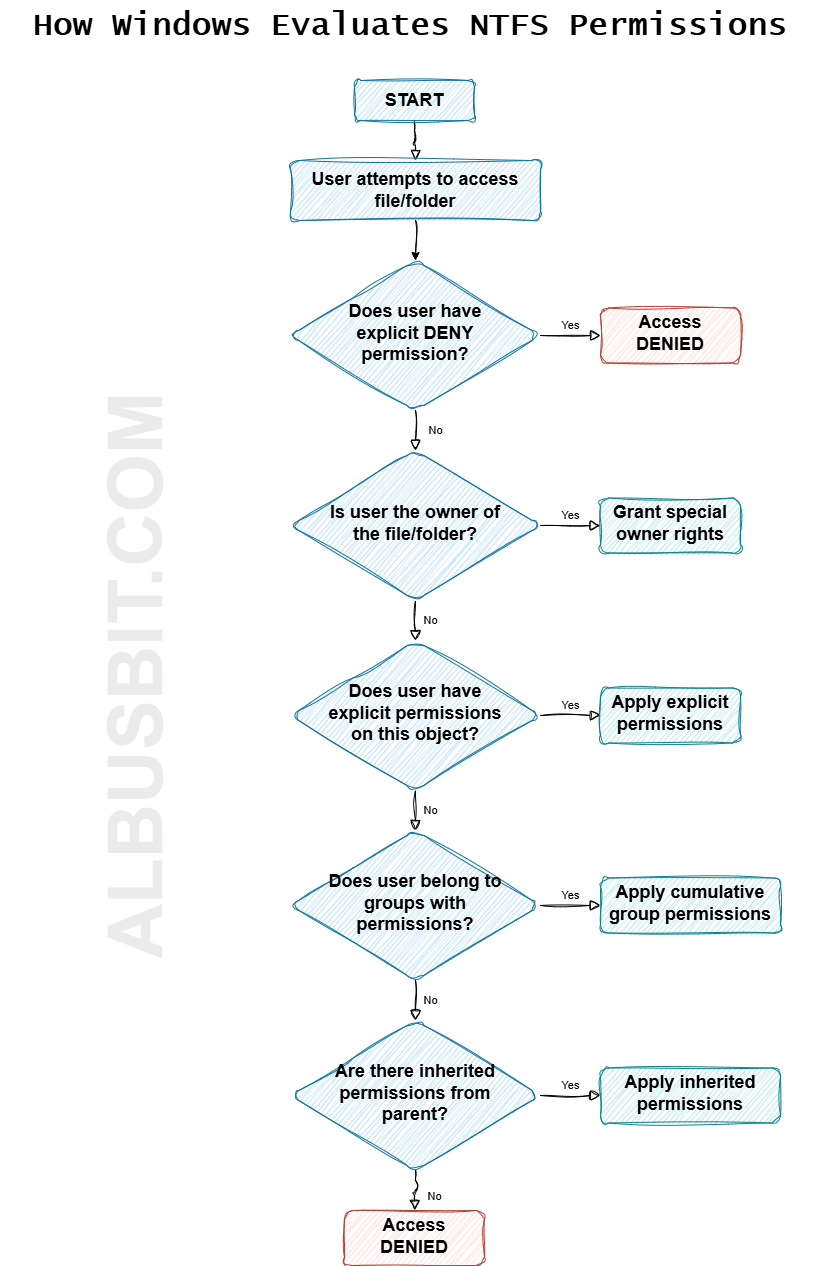
How NTFS Permissions Are Evaluated?
Understanding how Windows evaluates NTFS permissions helps troubleshoot access issues. The process follows these rules:
- Explicit denies override everything: If a user has an explicit Deny permission, it doesn't matter what other permissions they have—they will be denied access.
- Explicit permissions override inherited permissions: Permissions directly set on a file or folder take precedence over permissions inherited from parent folders.
- Permissions are cumulative: If a user belongs to multiple groups, they receive all the permissions from each group (except when denied).
- Child permissions can't exceed parent permissions: Users can't have more access to a subfolder than they do to its parent folder when accessing through the file path.
How can I set up NTFS permissions?
NTFS permissions can easily be set using Windows Explorer. Here’s how:
To set permissions for an object:
In Windows Explorer, right-click a file, or directory and click Properties.
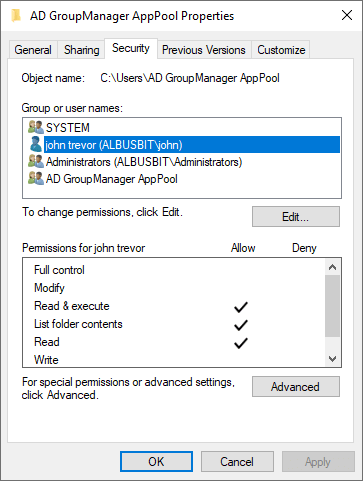
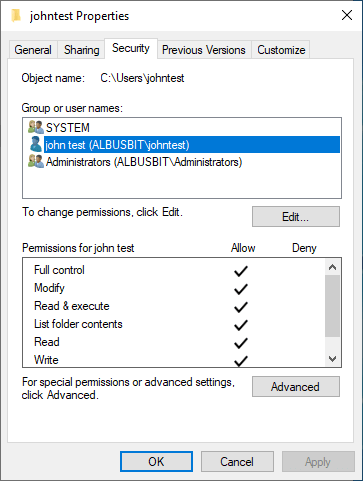
The Properties dialog box will then appear. Navigate to the Security tab. This is where you can set basic permissions.
In the top panel, we can see the list of groups and users. By default, this should show all the user groups you’ve previously configured for this system. You can add new groups and individual users by clicking Add.
Select the user or group you want to adjust permissions for and look down to the permissions section. Check and uncheck each basic permission as you see fit.
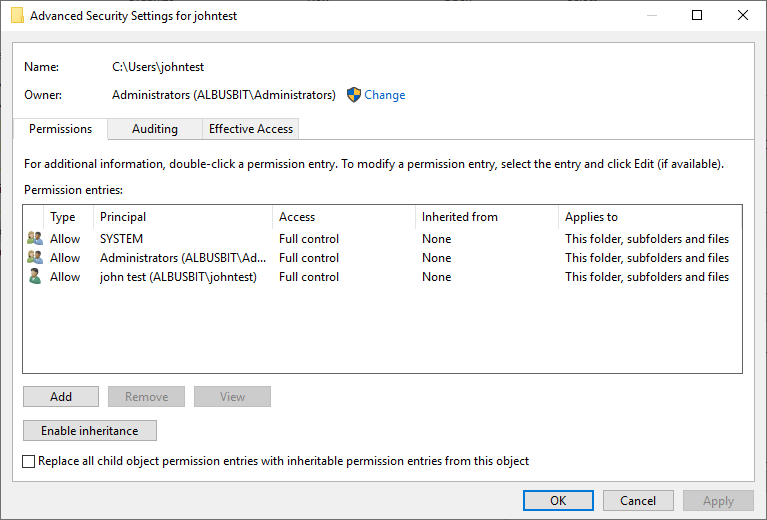
Need to access the special permissions? Click Advanced to open the Advanced Security Settings tab.
Click Add to dial in a new permission entry, or Edit to adjust an existing one.
Hit apply, and you’re done! Your NTFS file permissions have been configured.
How to Fix Common NTFS Permission Problems?
Even experienced administrators encounter NTFS permission issues. Here are solutions to the most common problems:
- Check for explicit "Deny" permissions that might be overriding your "Allow" permissions
- Verify you have permissions on all parent folders
- Check if the file is encrypted or in use by another process
- Ensure you're not being blocked by share permissions when accessing over the network
- Try taking ownership of the file or folder: Right-click → Properties → Security → Advanced → Owner tab → Edit → Select your user → Apply
- Ensure "Replace all child object permissions with inheritable permissions from this object" is checked when applying permissions
- Check for broken inheritance on subfolders
- Verify explicit permissions aren't overriding inheritance
- For large folder structures, try using icacls command-line tool:
icacls "C:\path\to\folder" /reset /T /C
If you've made permissions changes that are causing problems, you can reset to Windows defaults:
- Open Command Prompt as Administrator
- Navigate to the drive where the folder is located (e.g.,
cd /d D:) - Run the secedit command to reset permissions:
secedit /configure /cfg %windir%\inf\defltbase.inf /db defltbase.sdb /verbose - For a specific folder, use icacls:
icacls "path\to\folder" /reset /T
Warning: This will remove all custom permissions. Use with caution, especially on system folders.
What are some best practices for using NTFS permissions?
Here are some of our top tips and best practices for using NTFS permissions effectively:
Use groups instead of granting permissions to individual users. Assigning permissions to user groups is a far simpler and more robust way to handle Windows file permissions. When a user needs to be added or removed from certain permissions, all a system administrator will need to do is modify the user groups - not the individual NTFS permissions. Granting individual user permissions can be incredibly messy, and administrators tend to lose track of which permissions are granted to whom. Stick to user groups and save yourself the headache!
Don’t give users Full Control over directories. It’s best practice to avoid granting users Full Control over files and directories. Remember, the Full Control permission enables users to modify NTFS permissions. This isn’t something the vast majority of users will need to do - and this ability should be reserved strictly for the system administrator. Grant the Modify permission. This will do for most users.
Grant the most restrictive permissions needed for a user to carry out their work. Don’t be too generous with your file permissions. A system administrator should know exactly what a user needs access to, and what they should be able to achieve with the files and directories referenced. Assign the Read permission only to users who need to read files and not change, delete, or create files in the directory. If a user isn’t involved in any of the projects contained on a specific drive, they shouldn’t be able to read those files - let alone modify them.
Administrators should speak to line managers to figure out what access is needed. It’s much safer to add permissions when requested than be too generous and risk a data leak.
Frequently audit and stay current on all NTFS permissions. Remove unnecessary and outdated permissions.
NTFS Permission Best Practices for Businesses
Enterprise environments require additional considerations for effective permission management:
- Implement a folder naming convention that indicates security level
- Centralize sensitive data in specific locations
- Document your permission structure in a central repository
- Review and audit permissions quarterly
- Use Access-Based Enumeration to hide inaccessible files
- Implement Dynamic Access Control for attribute-based permissions
- Consider using File Server Resource Manager for quotas and file screening
- Enable auditing for sensitive directories
For clean group management, implement a three-tiered approach:
- Global Groups: Based on job roles (e.g., Accounting-Staff)
- Domain Local Groups: Based on resources (e.g., Accounting-Files-Modify)
- Nesting: Place Global Groups into Domain Local Groups
This approach (known as AGDLP) creates a flexible and manageable permission structure that scales with your organization.
How to audit and understand the current situation with NTFS permissions?
Going and manually checking the permissions of each directory is not a smart choice. Especially if you have to do this for an entire file server or even multiple servers and file shares.
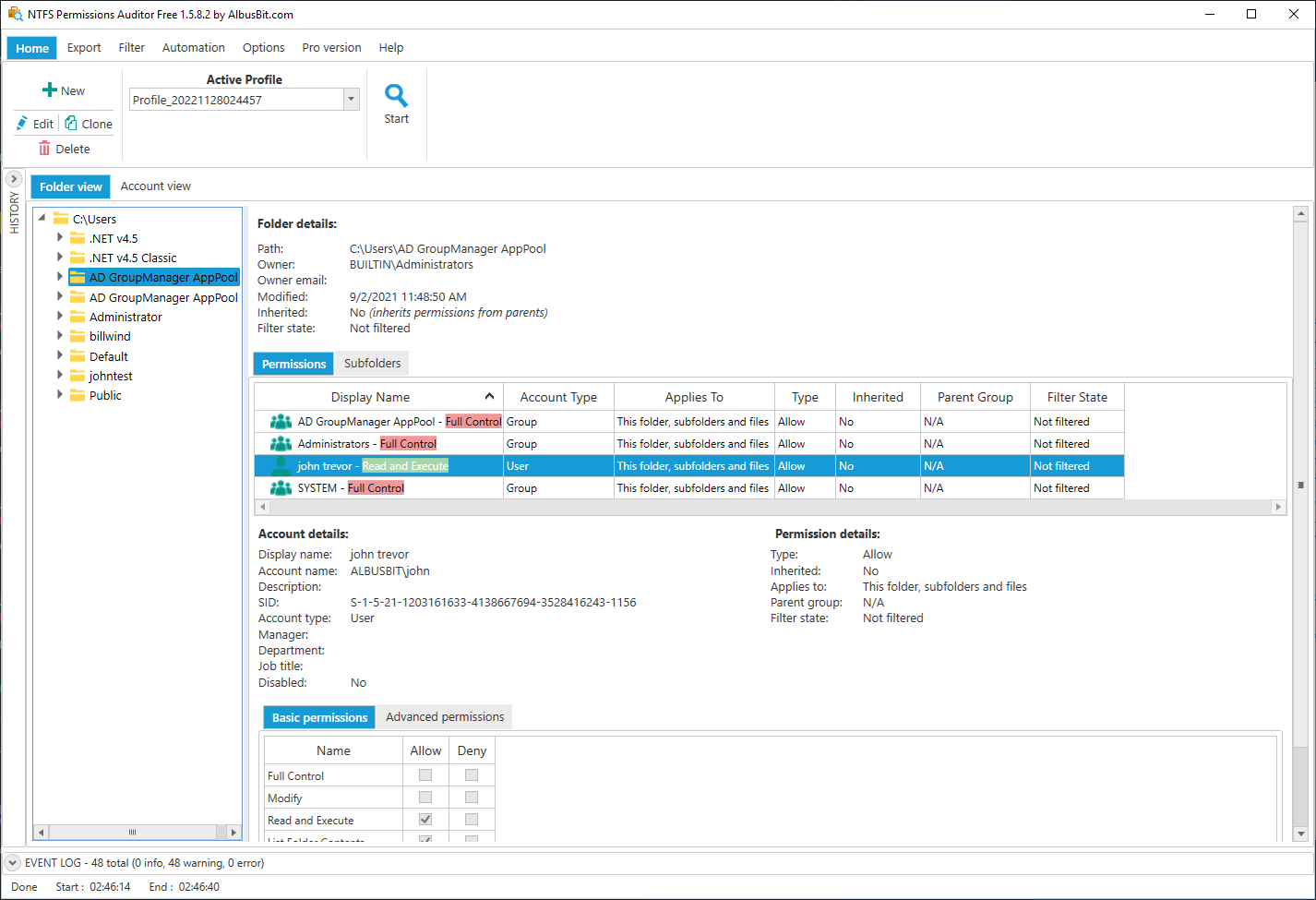
This process can be automated to save time and make your job easier. NTFS Permissions Auditor is a tool that you can specify audit paths and it will automatically check all folders and create transparent reports of your permissions for you. Download the free version here and get your first reports in 5 minutes.
Save Hours of Manual Permission Checking
Get a complete map of your NTFS permissions in minutes with our free auditing tool. No more guessing who has access to what files.
Why Audit NTFS Permissions?
Regular permission auditing helps you:
- Identify security risks from overly permissive access
- Ensure compliance with security policies and regulations
- Clean up unnecessary access from former employees
- Understand permission inheritance chains
- Document your security posture for IT audits
How to get NTFS permission report in 5 minutes? Download the free version and install it, below we set up the profile to start auditing.
Click on Create a configuration profile.
For the first audit, specifying the directories is sufficient. You can explore other profile settings later. We can Save changes and Start auditing.
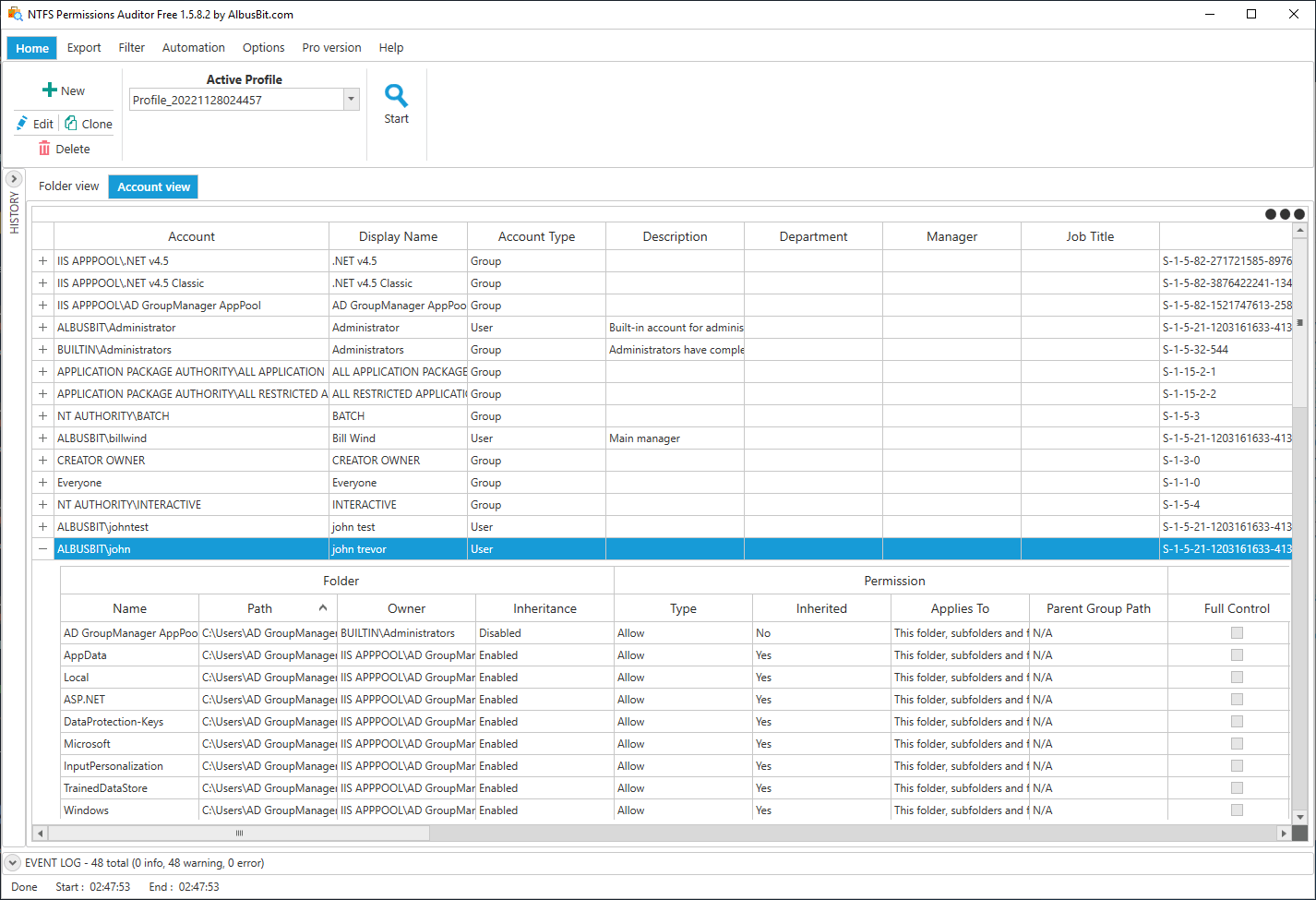
Results should be available within a few minutes, depending on the number of directories and the number of Active Directory users and groups. You can see a more detailed explanation of the data you see here.
Account view shows all security principals and their folder access rights. Each account row can be expanded to see folders if it has any kind of permissions.
Frequently Asked Questions About NTFS Permissions
When copying: The copied file inherits permissions from the destination folder.
When moving on the same volume: The file retains its original permissions.
When moving to a different volume: The file is actually copied, so it inherits permissions from the destination folder.
Yes, PowerShell provides powerful commands for managing NTFS permissions:
# Get permissions for a folder
Get-Acl -Path "C:\path\to\folder" | Format-List
# Grant permission to a user
$acl = Get-Acl -Path "C:\path\to\folder"
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule("DOMAIN\Username","Modify","Allow")
$acl.SetAccessRule($accessRule)
$acl | Set-Acl -Path "C:\path\to\folder"NTFS permissions and Encrypting File System (EFS) work together but serve different purposes:
- NTFS permissions control who can access files while they're stored on disk
- EFS encrypts file content so it can't be read by unauthorized users who might bypass NTFS security
- Users need both NTFS permission AND the encryption certificate to access encrypted files
- Administrators with Full Control permissions still need the encryption certificate to read encrypted files
Full Control is a permission that gives users complete access to read, write, modify, and delete files, but it doesn't automatically include the ability to take ownership.
Take Ownership is a specific advanced permission that allows a user to become the owner of a file or folder. The owner always has the right to change permissions, even if they don't have Full Control.
This distinction is important for security administration, as it allows for emergency access recovery without granting excessive permissions.
NTFS Permissions Cheat Sheet
Download our free NTFS permissions cheat sheet to keep these concepts handy:
Download NTFS Cheat SheetFinal Thoughts
NTFS permissions are a powerful tool for ensuring data security within a system or network. When implemented correctly, they create a secure yet accessible environment for your data. Remember these key takeaways:
- Use groups instead of individual permissions for easier management
- Implement the principle of least privilege—only grant what users need
- Understand how permission inheritance works to avoid unexpected access issues
- Regularly audit permissions to maintain security hygiene
- Document your permission structure for easier troubleshooting
NTFS permissions only work on drives that are formatted to NTFS. If you move files to another file system, you'll lose the permissions data.
Ready to master your file permissions? Start with a complete audit of your current environment. Download our free NTFS Permissions Auditor and see who has access to what in just 5 minutes.
Have questions about NTFS permissions or need help with a specific scenario? Contact our support team for personalized assistance.